articles
Computer Online Forensic Evidence Extractor (COFEE) is a software program developed by Microsoft for use by law enforcement. It was held closely by law enforcement for a period of time until it was revealed in the last year, and subsequently, several individuals released software intended to defeat the utility of COFEE. While a big deal has been made of the secrecy of this tool and other related matters, reasoned examination has been somewhat lacking in the open community, even though there have been validation studies undertaken of the tool. Thus this limited review of the situation is suited to this special end-of-year edition.
Basics of COFEE
COFEE is, according to its documentation, a collection of programs residing on a mountable media (typically a USB disk drive emulation) designed so that when the USB device is placed in a computer, the COFEE program executable can be run by the investigator. The program is intended to use minimal resources so as to alter as little as possible in the operating environment while allowing the collection of data such as the process, file, and network status, and so forth. It does this by presenting a simple user interface and running copies of other software programs contained on the USB device to collect data.In this sense, COFEE is really no different from programs like ForensiX or older menu-based systems for running programs, except that it is wrapped in a particular methodology and implemented on a USB drive to be useful for working on "live systems". There are many "live" forensics tools that do similar, or in many cases, what appear to be more forensically sound and larger collections of, jobs of extracting data from systems as they operate.
Programs run by COFEE
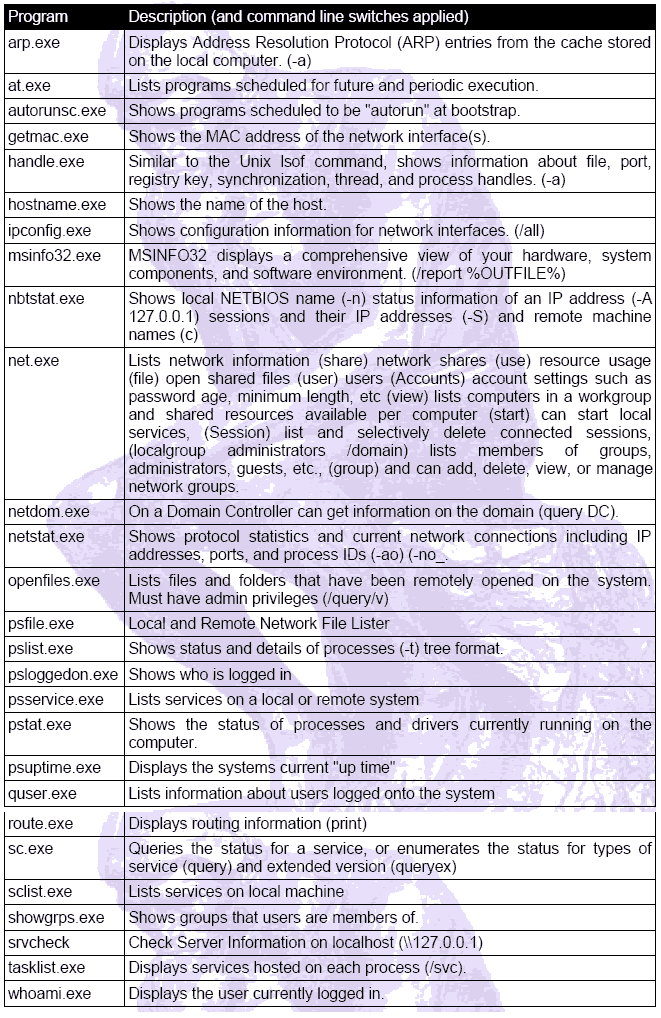
The programs that are, apparently, standard with COFEE, are the programs listed below, as documented within the distribution I retrieved from an Internet archive for the purposes of writing this report. These and similar programs have long existed in various operating environments, such as Linux, Unix, and Windows. Their operation is well known, source code for some versions of some of them may be available, and they can be examined individually for their properties. This also helps in the issues of authenticating their operation for legal purposes, as they are widely published and well known tools that are in widespread use on a day-to-day basis all over the world, and are generally relied upon for normal business purposes for the uses they are normally applied to. That is not to say that they are without flaws, but it is consistent with the normal legal processes associated with the use of tools and writings they produce for admissibility in legal proceedings.
Validation studies of COFEE
Unlike most software seen on the market, and unlike many software packages used in digital forensics today, independent validation studies have apparently been undertaken of some elements of COFEE. In particular, three such studies are included in the distribution:- "COFEE v1.1.2 GUI CONSOLE - Validation Study" 9/29/2009 by Mark Bowser, CFCE, and Justin Wykes, CFCE, both Computer Crime Specialists at the National White Collar Crime Center.
- "COFEE version 1.1 Runner and NW3C Profiles - Validation Study ", 9/02/2009 by Charles Matt Weir, CISSP and Sri Harsha Angara, Graduate Research Students Florida State University.
- "COFEE v1.1.2 - Runner & NW3C Profiles - Validation Study", 9/29/2009 by Justin Wykes, CFCE and Mark Bowser, CFCE, both Computer Crime Specialists at the National White Collar Crime Center.
Study 1 was undertaken under a US Department of Justice Federal grant. "This validation study was conducted to verify COFEE properly formats, wipes, and generates profile(s) to a thumb drive, including its ability to generate a report from collected data. This validation study was conducted to ensure that COFEE consistently completed all of its required actions." The study concludes that COFEE passed all of the tests it was given, and more specifically, that it "successfully generated a listed profile, a user created profile, formatted an attached device as FAT 32 and overwrote or wiped data existing in unallocated space on the device. COFEE successfully generated a detailed report of the results of the collected data from a specified profile. There were no unexpected anomalies found during testing." A list of 18 assertions were identified for testing, and one test environment was configured for the validation. These assertions largely portray the specifics summarized above, and tests included verification that formatting of the drive fails when inadequate space is present and gives a proper error notice. This study did not provide any useful details about performance of the other functions, and makes no particular assertions about tool use, alterations to the target system, or the correctness of results, other than the performance of specific actions by the interface program as identified therein.
Study 2 defines itself well; "COFEE's primary purpose is to create a thumb drive which contains a pre-determined set of applications which are set to run on a suspect's live machine. Upon connecting a COFEE generated thumb drive to a suspect's machine, the investigator executes runner.exe (a program located on the thumb drive) which, in turn, executes all of the programs specified by COFEE, and stores the data collected on the investigator's thumb drive. The programs placed on the generated thumb drives are identified by a "profile" loaded into COFEE. While any user can create their own profile, this validation study will focus only on the profiles created by NW3C: "NW3C - Volatile Data" and "NW3C - Incident Response." This validation study was conducted to ensure that when runner.exe is executed: all of the programs identified by the profile are executed, that the collected data is stored on the investigator's thumb drive, that no applications were run from the suspect's machine, and that no unacceptable writes were made to the suspect's machine. COFEE is currently only supported on the Microsoft Windows XP operating system. No other operating system was tested during this validation study."
The conclusions from this study were a bit over the top, as we will soon see, but for two graduate students, this represents a reasonably strong effort. They conclude "Testing conducted on Runner and the NW3C profiles verified that both the runner.exe application, as well as the selected programs, functioned as expected and are well within acceptable practices for data collection on a live system." ... "NW3C - Volatile Data Profile - There wereno writes to the suspect drive's file system using this profile. There were updates made to the Windows Registry on the suspect's machine, however none of the registry updates were of obvious forensic value." ... "NW3C - Incident Response Profile - This profile attempted to make five writes to the target computer's file system. Three of the writes were caused by the program handle.exe and were made to the file "PROCEXP100.sys." The reference to the file PROCEXP100.sys is hard-coded into handle.exe, a product of Sysinternals, and as such it is not possible to restrain handle.exe from writing to this file. However, this file is specifically written as part of the Sysinternals' toolset and is unlikely to be of any evidentiary interest. The other two attempted writes were made to network shares on the target computer, and were also unlikely to be of any evidentiary interest. There were also updates made to the Windows Registry on the suspect's machine, however none of the registry updates were of obvious forensic value."
This study used 3 different configurations of computers, and tested the following conditions:
Dr. Frederick Cohen, Ph.D., and his associates have recognized expertise in E-Discovery, Digital Forensics, Computer Security, Information Protection, and Related Areas. For more than 30 years, they have served as an unbiased independent source of top quality information in this arena.
See Dr. Cohen's Profile on Experts.com.
©Copyright - All Rights Reserved
DO NOT REPRODUCE WITHOUT WRITTEN PERMISSION BY AUTHOR.


